International | LNG | LNG Insight | NGI All News Access | NGI The Weekly Gas Market Report
U.S. Oil, Natural Gas Seen Vulnerable as Cybersecurity Threats Grow Amid War in Ukraine
The U.S. government reiterated warnings this week that Russia could be preparing cyberattacks in response to economic sanctions for its war in Ukraine, raising yet another alarm for the American oil and natural gas industry and other critical infrastructure operators.
The announcement perpetuates what’s been an ongoing threat for the oil and gas sector since late last year, when Russia began building troops along Ukraine’s border. The White House on Monday cautioned the private sector to be prepared, citing intelligence reports that the Russian government is “exploring options” for potential cyberattacks.
The FBI also reportedly warned the U.S. energy sector earlier this month of cyber threats from Russian-based actors previously implicated in attacks on critical infrastructure overseas. The warnings followed a similar one earlier this year from U.S. intelligence agencies.
A spokesperson for the Interstate Natural Gas Association of America told NGI that the industry group has been closely monitoring the situation with its members since January and is working with the federal government to implement protective measures.
Since oil and natural gas operations ensure a reliable supply of energy for other crucial sectors, the industry is considered more vulnerable to cyberattacks.
‘Potential Threat’ Heightened
“I think the awareness of the potential threat has heightened,” said the American Petroleum Institute’s (API) Suzanne Lemieux, director of operations security and emergency response policy. “Geopolitically, I think we’re all aware that energy is a target because of Russia’s market share in oil and natural gas resources in particular.”
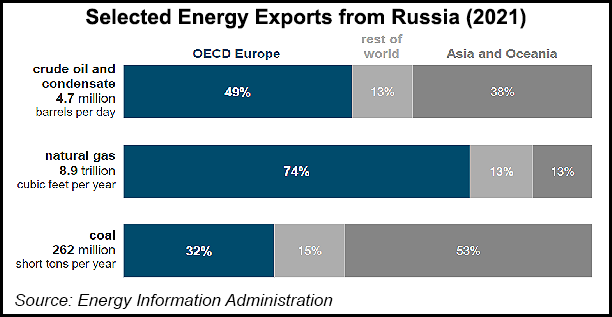
While the West has levied economic sanctions and limited measures against Russian commodities, it has largely excluded energy exports from those measures. Many of the world’s buyers, however, have self-sanctioned and limited purchases of Russian oil and natural gas, impacting a key source of revenue for the country.
Europe has also announced plans to reduce its reliance on Russian natural gas imports. U.S. liquefied natural gas (LNG) exports to Europe have surged over the last three months, accounting for roughly half of all volumes that arrived on the continent in January and February. The ongoing shift in global energy markets squarely places a target for cyberattacks on U.S. LNG export facilities in particular.
Bloomberg reported last month that hackers managed to gain access to the computers of current and former employees at 21 U.S. energy companies, including Chevron Corp., Cheniere Energy Inc. and Kinder Morgan Inc. A group with ties to the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation, often referred to as the GRU, was offering to pay for access to the computers, according to the Bloomberg report.
Lemieux told NGI that no access was gained to company networks in that instance. Kinder Morgan also told NGI that no corporate computers or passwords were compromised.
Increasing Activity
Efforts to gain such access are not uncommon, but as fighting has intensified in Ukraine and Western governments have stepped up their response, activity is on the rise. The White House said Monday that while no specific cyberattack has been identified, preparatory activity for such an event has increased.
“There’s a whole lot of preparation that has to be done,” to execute a cyberattack, said Dennis Underwood, CEO of ransomware protection firm Cyber Crucible Inc. Underwood told NGI that setting up for a cyberattack is “kind of like sabotage, where there needs to be a lot of preparation to get saboteurs in place behind enemy lines.”
There is no guarantee an attack will take place, but he added that activity has been ramping up for months.
Industrial cybersecurity firm Dragos said in a report this month that the cyber risk oil and gas companies face in North America is increasing. Dragos tracks seven activity groups that target oil and gas operations. One of those is known as Kamacite, which has links to the GRU and participated in cyberattacks that caused blackouts in Ukraine in 2015 and 2016.
Dragos stressed that any point across the oil and gas supply chain is vulnerable to cyberattacks. Lemieux agreed, saying none is more vulnerable than the other, particularly as a shadow war has unfolded against criminal actors and nations like China, Russia, Iran and North Korea that have increasingly focused on U.S. targets.
“I don’t think you need to have one particular vulnerability,” she said. “It’s the persistence of the threat actor that is going to be your biggest vulnerability.”
Cyberattacks pose a broad range of threats to the energy sector. High costs can come with ransomware attacks, intellectual property can be stolen, or a debilitating attack on vital equipment could disrupt supply chains or prove catastrophic. Most recently, Colonial Pipeline Co., a major supplier of gasoline and jet fuel to the eastern United States, halted operations in May after learning it was the victim of a ransomware attack.
“If you take the geopolitical considerations, energy is probably where the biggest threat is” for Russian President Vladimir Putin. “For Russia, that is a major cash source, and I could see that being a heavily targeted space that would have a disruption,” Underwood said. “They’re going to try to infiltrate something that has a bigger effect on society.”
Unlike the power sector, however, the oil and gas industry doesn’t face the same sort of cybersecurity standards, leading some to call for stricter regulations. Rep. Bobby Rush (D-Ill), chairman of the House energy subcommittee, has introduced a bill that would require the Federal Energy Regulatory Committee to mandate cybersecurity standards for oil and gas operators.
Lemieux said cybersecurity has been a top priority for the industry for decades. She said API members have strengthened their defenses in recent months, followed federal guidelines and worked with U.S. officials since late last year when tensions between Ukraine and Russia neared a boiling point.
“We’re facing well funded, nation-state threats,” she said. “Regardless of the target, it’s really the level of effort put in by the threat actor. We’re all going to be compromised at some point, and we’re doing everything we can to mitigate those impacts and defend against them.”
© 2024 Natural Gas Intelligence. All rights reserved.
ISSN © 1532-1231 | ISSN © 2577-9877 | ISSN © 1532-1266 |