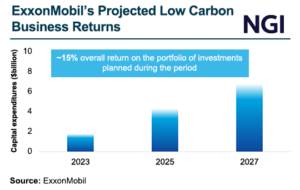
As the United States has become the world’s largest producer of oil and natural gas, cybersecurity concerns in the sector have shifted from primarily protecting intellectual property to guarding against potential attacks from rival nations, an expert told NGI.
“Intellectual property theft is still a concern; it could be from a criminal element or a nation state,” said American Petroleum Institute’s (API) Suzanne Lemieux, manager of operations security and emergency response policy.
But the “geopolitical aspect is relevant today” as critical infrastructure to discover, produce, transport and refine U.S. hydrocarbons gas become increasingly reliant on advanced technology and automation to reduce costs, Lemieux said Wednesday.
The domestic oil and gas industry has...